What is a Phishing attack?
Phishing attack is a type of digital attack used to steal data of users.
This is a type of attack which is completed with the help of internet. The
attackers used to steal credit card numbers, bank details and many confidential
data. It occurs when an attacker, send an E-mail or any message looking like a
trusted source, and the receiving user open it and enters his/her personal
details. They send messages like “you won a gift voucher from the
bank” or “we have noticed some unwanted movements in your bank account, so
please click here and fill the asked details”. The beneficiary is then fooled
into clicking a malevolent link, which can prompt the establishment of malware,
the freezing of the framework as a feature of a ransomware assault or the
noteworthy of delicate data.
“Phish” is pronounced just like “fish”. But there is a difference,
during fishing we catches fish but during Phishing attackers catches us, for
their benefit. The similarity is of a fisher tossing a bedeviled snaring out
there (the Phishing email) and you trust to catch it.
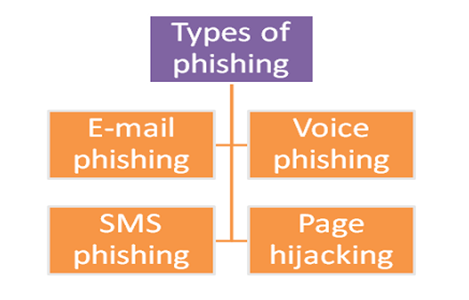
1. Email Phishing
Most Phishing messages are conveyed by email, and are not customized or focused on to a particular individual or organization this is named "mass" Phishing. The substance of a mass Phishing message changes generally relying upon the objective of the assailant normal focuses for pantomime incorporate banks and monetary administrations, email and cloud efficiency suppliers, and real time services. Attackers may utilize the certifications acquired to straightforwardly take cash from a casualty, in spite of the fact that undermined accounts are frequently utilized rather as a hopping off highlight perform different assaults, like the burglary of restrictive data, the establishment of malware, or the lance Phishing of others inside the objective's organization. Compromised web-based feature accounts are typically sold straightforwardly to purchasers on darknet markets.
2. Voice Phishing
Voice Phishing is also known as vishing. It is the utilization of communication to lead Phishing assaults. Assailants will dial an enormous amount of phone numbers and play robotized chronicles - regularly made utilizing text to discourse synthesizers - that make bogus cases of deceitful action on the casualty's financial balances or MasterCard. The calling telephone number will be mock to show the genuine number of the bank or foundation mimicked. The casualty is then coordinated to call a number constrained by the assailants, which will either consequently incite them to enter delicate data to "determine" the alleged extortion, or interface them to a live individual who will endeavor to utilize social designing to acquire information. Voice Phishing profits by the lower mindfulness among the overall population of strategies, for example, guest ID mocking and robotized dialling, contrasted with the reciprocals for email Phishing, and along these lines the innate trust that numerous individuals have in voice communications.
3. SMS Phishing
SMS Phishing is also known as smishing. It is thoughtfully like email Phishing, with the exception of aggressors use PDA instant messages to convey the 'bait'. Smashing assaults regularly welcome the client to click a connection, call a telephone number, or contact an email address given by the assailant by means of SMS message. The casualty is then welcomed to give their private information; regularly, certifications to different sites or administrations. Moreover, because of the idea of portable programs, URLs may not be completely shown; this may make it harder to recognize an ill-conceived logon page. As the cell phone market is currently immersed with cell phones which all have quick web network, a malignant connection sent through SMS can yield a similar outcome as it would whenever sent by means of email. Smishing messages may come from phone numbers that are in an odd or startling format.
4. Page hijacking
Page hijacking involves compromising legitimate web pages to redirect
users to malicious websites or cross-site scripting exploit kits. A hacker may
compromise a website and insert an exploit kit such as MPack in order to
compromise legitimate users who visit the now compromised web server. One of
the simplest forms of page hijacking involves altering a webpage to contain a
malicious inline frame which can allow an exploit kit to load. Page hijacking
is often used in conjunction with a watering hole attack on corporate entities
to compromise targets.
An example of Phishing:
· A user is having its account in XYZ Bank.
· He receives an email from a source looking just like his bank’s
professional email.
· We have noticed some unwanted things in your bank account. If this
wasn’t you so please click on the link given here and update some information
asked there.
· User clicks on the link and fills all the information.
· After some time he noticed some money deduction from his account.
So this was the example of Phishing.
How to prevent Phishing?
For undertakings, various advances can be taken to relieve both Phishing
and lance Phishing assaults:
·Two-factor confirmation is the best technique for countering
Phishing assaults, as it's anything but an additional check layer when signing
in to touchy applications. Two-factor confirmation depends on clients having
two things: something they know, for example, a secret phrase and client name,
and something they have, for example, their cell phones. In any event, when
representatives are undermined, Two-factor confirmation forestalls the
utilization of their undermined accreditation, since these by themselves are
lacking to acquire passage.
As well as utilizing Two-factor confirmation, associations ought
to implement exacting secret word the board strategies. For instance, workers
ought to be needed to regularly change their passwords and to not be permitted
to reuse a secret phrase for different applications.
Instructive missions can likewise help lessen the danger of
Phishing assaults by authorizing secure practices, for example, not tapping on
outer email joins.
What is the common reason behind the Phishing attacks?
Lack of security awareness is the main reason behind the phishing
attacks. We should first check and make sure that is this really from the
genuine source or not.
Articles you can read:
click here to know about Dark Web.
click here to know what is a
malware
Click here to know how to find
your lost phone?
economics
Click here to know what is e
commerce?